Table of content
The Litepaper is subject to change, we update as we progress.
The only effective weapon against “big tech” is “small tech decentralized”
Jeff Bouchard, CBBF, CBSA, privateness.network, emercoin.com/team, @skywire
1. Introduction: The Problems
- 1.1 Privacy & Neutrality: Balkanisation of the Internet;
- 1.2 Interoperability: Balkanisation of Blockchains;
- 1.3 The Rise of Totalitarianism.
2. The Solution: PrivateNess Network
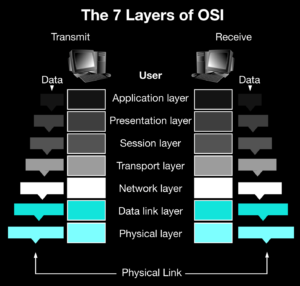
- 2.1 A fully Decentralized and Obfuscated OSI protocol stack
- 2.2 Uniqueness & Determinacy
- 2.3 Non-interactiveness
- 2.4 We don’t put all our Trust in the same basket
- 2.5 More about UHE PRNG
- 2.6 This generator effectively never repeats
- 2.7 More on Randpay
3. Main Platform: Skycoin Fiber
4. EmerNVS for Blockchain-as-a-Service
5. CoreNode authentication by NFTs
- 5.1 Proof of ownership
- 5.2 Differences between mining and masternodes
6. NESS coin supply distribution
7. Roadmap 2021-2022
- 2021 Q3 13
- 2021 Q4 14
- 2022 Q1 14
8. Sources & Further Reading
1. Introduction: The Problems
1.1 Privacy & Neutrality: Balkanisation of the Internet
About Net Neutrality:
As of June 11th of 2018, the legal protections against content discrimination on the internet are gone.
As far as the FCC is concerned, net neutrality is dead.
The policy’s fate was sealed back in December 2017, when FCC chairman Ajit Pai’s Restoring Internet Freedom Order was approved in a 3-2 vote along party lines. Pai’s order, which goes into effect today, rolls back the net neutrality protections that were put in place by former chairman Tom Wheeler. They promise — in name, at least — unrestricted access to online content minus the burden of regulation. But in fact, the new ruling clears the way for massive internet service providers to do practically whatever they like — including paid prioritization, throttling, and otherwise messing with traffic as it moves across the internet. It will take a long time to see the practical effects of the new rules, but make no mistake: this is a big deal, and it’s the first step in a long, slow process that will reshape the internet in very ugly ways.
About the Balkanization of the Internet: Catalysts for Fragmentation:
Power tends to corrupt, and absolute power corrupts absolutely
The global internet is the US internet
Despite its global reach and cosmopolitan contributor base, the internet and the Web remained firmly under US corporate auspices, and therefore US government control. This historical reality is the root cause of cyberbalkanization.
Centralized Data is the new oil
If the US has a “home field advantage” through control of internet traffic routing, so does it have an “away field” advantage by controlling the AI-powered data mining power of world’s most popular web service platforms.
Snowden and the US global surveillance apparatus
Snowden’s revelations laid bare the vulnerability of foreign nations to US espionage, which was occurring at multiple levels from the data transmission layer to the web service layer. From a US perspective, the NSA mass surveillance program is a logical utilization of its power as the gatekeeper of the modern internet. By maintaining supreme control over internet traffic flow and web service user data, the US gained enormous strategic advantages in its effort to maintain its status as the world superpower. Any nation wielding such power would be rationally expected to act in a similar manner. There is no reason to believe that US tech giants have stopped collaborating with the US intelligence agencies in data sharing and surveillance programs.
There is no reason to believe that US tech giants have stopped collaborating with the US intelligence agencies in data sharing and surveillance programs
The rational case for cyber-secession
The component causes of cyberbalkanization effectively distill into a single necessary cause — the US control of the creation, storage and transmission of online data. What was previously a community-built highway is now a toll road operated by a single gatekeeper of overreaching influence and power. Allies and rivals alike have begun efforts to break free from the US-controlled cyberspace in an effort to protect their informational sovereignty as an urgent matter of national security. A future of siloed, firewalled and incompatible internets is upon us and this rapid acceleration towards cyberbalkanization is being spearheaded by China, Russia and Europe.”
Balkanization Now, The rise of the internet ‘walled gardens’
- China maintains a completely independent internet ecosystem which is maintained by the dictate of the Chinese Communist Party. The Great Firewall of China defends Chinese cyber borders and facilitates censorship of citizens by blocking access to content undesirable to the Chinese government. Perhaps more importantly, the Great Firewall keeps the data of Chinese citizens, businesses and military beyond the reach of the US surveillance apparatus. China stands as the only the nation to have successfully broken free from US internet and telecommunication dominance while demonstrating the potential for economic prosperity. It exists as the most fully formed Cyberbalkanized nation.
- In 2014, the Russian national security body commissioned the Russian Government to create an independent internet for the BRICS bloc (Brazil, Russia, India, China and South Africa) that would exist beyond the sphere of Western influence. Russian press secretary Dmitry Peskov stated “We all know who the chief administrator of the global internet is. And due to its volatility, we have to think about how to ensure our national security…It’s not about disconnecting Russia from the World Wide Web, it’s about protecting it (Russia) from possible external influence.”
- The trend towards cyberbalkanization is not only being observed among US rivals. The Snowden leaks revealed US spying on its Western allies, who are beginning to assert their informational sovereignty. Rather than create their own social media companies, Europe is gaining control of its citizens’ data by exerting soft power over US web service giants by means of legal action and fines. The infamous General Data Protection Regulation (GDPR) mandates the storage of EU citizens’ data to be stored on servers located within the EU borders. As the US threatens to redraw the global geopolitical border with anti-NATO rhetorics, the online world is beginning to mirror the political and national contours of the physical world.
- The recent German legislation known locally as NetzDG perfectly illustrates the dual consequences of cyberbalkanization — foreign espionage protection and domestic censorship. This act allows Germany to fine internet giants like Facebook, Google and Twitter up to 50 million Euros for failing to remove illegal content from their platforms within 24 hours. As is expected of any absolute dictate, the definition of “illegal” is increasingly arbitrary and susceptible to slow but inevitable restrictions on freedom of speech.
The perils of a Cyber Balkanized world
How might we imagine a Cyber Balkanized future in which the global cyberspace commons becomes fragmented across national and geopolitical boundaries? The major cyber blocs will continue to build domestic internet industries that route all traffic and store all user data internally. This will exacerbate a data siloing effect, restricting information flow across borders and rendering web services unusable from external geographic locations.
Cyberbalkanization will fundamentally be a triumph of the state over the individual right to free expression, free access to information, and freedom from intrusive surveillance. Unimpeded cyberbalkanization has the potential to unwind the prosperity gains achieved in the decades since the creation of the internet and the Web, contributing to the emergence of conflict between nations unseen by the current generation.
In the face of inevitable cyberbalkanization that heralds nationalistic isolation, mistrust and eventually open conflict. The creation of a new internet is therefore an urgent and timely undertaking on which the hopes of the free world rest. Cyberbalkanization will fundamentally be a triumph of the state over the individual right to free expression, free access to information, and freedom from intrusive surveillance.

1.2 Interoperability: Balkanisation of Blockchains
About Avoiding Blockchains Balkanization: Prioritizing Interoperability
We define “interoperability” here as the ability for blockchains to exchange data between platforms—including off-chain data and transactions—without the aid of third parties. By examining the progress of Web2 architecture from early theory to mass adoption, we argue that blockchain protocol interoperability is nothing short of a fundamental requirement to realize the full potential of the technology. In the face of competition and commercial pressure, the ecosystem is currently in danger of “Balkanization”—i.e. becoming a series of unconnected systems operating alongside, but siloed from each other.
In order for the ecosystem to prioritize interoperability, it must establish a secure, radically decentralized, and trustless settlement layer onto which simultaneously-operating blockchains can anchor their transactions.
You never change something by fighting the existing reality, to change something, build a new model that makes the existing model obsolete
The Risk of Balkanization (yet again)
The problems of today’s Web2 architecture—in particular the siloing, vulnerability, and mismanagement of user data—are traceable to the deviation of the industry from early Internet values, which originally prioritized interoperability as a key to a sustainable and equitable web-connected world. At its current pace, the blockchain ecosystem is at risk of similar “balkanization,” where protocol interoperability is deprioritized as companies race to demonstrate their own blockchain’s use case quicker than their competitors’.
The risk is that the pressures for mainstream adoption could arrive before the Web3 infrastructure is sufficiently interoperable and secure to manifest the full vision of its original architects. Web3 could end up looking much like Web2 does today in terms of financial exclusion, information siloing, and data insecurity; Underwritten by a series of blockchains which by competitive design do not interoperate at the protocol level.
An attempt in the early 1990s to avoid balkanization of the Internet eventually resulted in accidental, extreme centralization in which a cabal of five infrastructure providers gained control of the entire protocol layer. In one sense, this is a lesson in the importance of native governance protocols and of reasonable regulation in developing healthy markets for new technologies. Good regulation that results in fairer, more open competition ultimately results in a richer market overall. Some retention of public interest also introduces a feedback loop of checks on the development of a novel technology as it scales. One shortcoming of the private infrastructure layer as it took shape was that insufficient attention to security, where it had not been as critical a concern; no security mechanisms nor R&D into security issues generally introduced vulnerabilities that still exist today [source]. The almost total lack of intentional governance has also resulted in the extreme lack of so-called “net neutrality,” hence unfair prioritization of network speeds to the highest bidder and vastly unequal access to networks overall.
Measures taken to prevent balkanization instead resulted in an all-but-irreversibly balkanized infrastructure layer
Too late for this Internet, it’s broken beyond repairs and upcoming regulations to advance totalitarian control over everything and everyone will finish the job…
The consequences of information being siloed in the blockchain in which it was created are straight from the history books of the Internet: The Internet centralized at the infrastructure layer due to scaling pressures to meet public enthusiasm and mass adoption.
Should the Web3 ecosystem reach that point before protocol interoperability is sufficiently pervasive, the same thing will happen again. Without native blockchain interoperability, third parties will step in to manage the transfer of information from one blockchain to another, extracting value for themselves in the process and creating the kind of friction the technology is meant to eliminate. They will have access to and control over that information, and they will have the ability to create artificial scarcity and inflated value.
The vision of a blockchain-powered Internet future the industry so often evoked is nothing without interoperability. Without it, we will find ourselves in a future with a global network nearly identical to the dominant Web2 landscape today. Everyday consumers will still enjoy their smooth and consistent interaction with Web3, but their data will not be secure, their identity will not be whole, and their money will not be theirs.

1.3 The rise of Totalitarianism
Surveillance capitalism is best described as a coup from above, not an overthrow of the state but rather an overthrow of the people’s sovereignty and a prominent force in the perilous drift towards democratic deconsolidation that now threatens Western liberal democracies. Big-data companies present the future as a new era of transparency and freedom. In fact, the end-point of information capitalism is a social order that can only be described as totalitarian.
Industrial capitalism depended upon the exploitation and control of nature (with catastrophic consequences that we only now recognise). Surveillance capitalism depends instead upon the exploitation and control of human nature
Back in the 1980s and 1990s, as the world moved broadly toward individualism, free-agency, smaller government, and globalism. The tech breakthroughs of that era were mainly deemed supportive of such libertarian trends.
Just after the Tiananmen Square massacre, Ronald Reagan declared that “the Goliath of totalitarianism will be brought down by the David of the microchip.” But in recent years, the world has been moving in a very different direction—toward community, populism, centralized control, and nationalism. Not coincidentally, today’s tech breakthroughs are again moving in tandem—toward empowering the group, not the individual (who now understands he is the product, not the customer).
The digital revolution was meant to emancipate. In the Declaration of the Independence of Cyberspace from 1996, John Berry Barlow declares the new digital reality, Cyberspace, to be an independent new world of freedom and equality without oppression of the old world of nation-states ruled by governments. Barlow compares the digital revolution to the American War of Independence and the pioneers of digitalization to the heroes of the American Revolution: “… those previous lovers of freedom and self-determination who had to reject the authorities of distant, uninformed powers.”
The digital reality that came to pass the following years and we are now in the midst of is far away from the digital utopia of liberation and self-determination. The Internet and the digital technology may just as well pave ways for new forms of oppression and dominion. Instead of being a force of democratization and emancipation, the digital revolution may turn out being the opposite and contribute to undermine democracy and political self-determination.
Digitalization and the Internet have enabled such massive data collection that surveillance may be almost total with no angles out of sight or blind spots: an updated digitized version 2.0 of Jeremy Bentham’s Panopticon (“all-seeing”) where one’s life is being monitored in detail 24-7 without any possible refuge from the gaze of the authorities.
In the Panopticon, privacy is not an option
Jeremy Bentham’s original architectonic plan for a Panopticon. A prison in which inmates are monitored constantly with no blank spots in the cells to hide from the Guards’ gaze. Whether the surveillance takes place in institutions such as prisons, schools, hospitals, the workplace, the army or is generalized to the whole society, it aims at the same result: the production of obedient subjects who conform to what is expected and wanted by the authorities—normalized and law- and norm-abiding citizens.
It does not necessarily require an authoritarian state aiming at social order and harmony as a primus motor to reach totalitarian conditions. An unregulated market for data and user information and the hunt for profits may be sufficient. Google is leading the way in a race and mission of colonizing, commodifying, and monetizing every aspect of our life.
The same year China initiated the construction of the Social Credit System, 2014; on the other side of the Pacific Ocean in Silicon Valley, Hal Varian, chief economist at Google, held a speech addressing the great opportunities made possible by extraction of data combined with massive processing power. The speech revealed a vision for a future of a surveillance capitalistic society with no more room for privacy than in China. According to Varian, the elimination of privacy is the (fair) price to pay, not for social order and harmony, but for the functionality, efficiency, and convenience of the products and services Google provides to the users.
Gathering and analyzing information about the user is the condition for personalizing the products for the user. Privacy is exchanged for enhanced user experience and the convenience made possible by personalized optimization and customization of the products that automatically tailor them to the individual user. Only when Google knows at least your location, budget, and food preferences, it is able to provide a relevant suggestion for a restaurant nearby to have dinner. The more personal information Google possesses, the more efficiently and conveniently it is able to serve one’s individual needs and demands.
That is the basic justification of the surveillance. However, even more surveillance, data mining, and information gathering are necessary to realize the tech giant’s vision. The ambition is that Google products should run so smoothly and conveniently for the user that it is not even necessary to google or ask Google questions. As company founder, Larry Page is quoted for saying:
[Google] should know what you want and tell it to you before you ask the question.
The prototypes of surveillance capitalism are Google and Facebook, which extract information from their users and deploy it to re-engineer their behaviour for maximum profit. Human experience is raw material to be mined. Individual autonomy is usurped by ubiquitous monitoring, with techniques of behaviour modification digging deep into what was once a private and subjective world. Personal experience is commodified, and reshaped in the interests of capital. Whatever utopian claims may have been made for it as a force that emancipates individuals, this is a type of collectivism that subverts what has in the past been described as free will.
This is a type of collectivism that subverts what has in the past been described as free will

2. The Solution: PrivateNess Network
GRC’s Ultra–High Entropy PRNG with PrivateNess dual fast-finality deterministic cryptocurrencies meet Emercoin to abstract, obfuscate and over-deliver on the task at hand. We use the carefully designed Ultra-High Entropy PRNG based on Latin Squares that utilizes more than 1536 bits of internal “state” memory made FOSS by Gibson Research Corporation. Easily overlooked are the intrinsic benefits of Randpay’s Blum’s “coin-flipping-by-telephone” problem resolution provided. Zero-Trust in the purest sense of the term where Trust is well-placed: start and stop at one self from the consumer perspective.
“Trust no One, Trust Anyone” meaning has evolved since Turing-completeness, with regards and respect to ARPA Chain (Blog: ‘ARPA Threshold BLS Random Number Generator Design’).
2.1 A fully Decentralized and Obfuscated OSI protocol stack
PrivateNess Network’s NESS token is a dual coin Fiber chain cryptocurrency on the Skycoin platform and equipped with Emercoin core (EmerNVS) as a local BaaS provider through json-rpc endpoints. The two technologies will be working side-by-side in a SHA-256 signed public-key to public-key communication scheme, unaware of one another in a kind of Double-Blind operation. Communications are limited to json-rpc respective endpoints restricted to 127.0.0.1 hence dramatically reducing surface and attack vectors. To the best of our current knowledge, this architecture has no functional limitations of any kind, no single point of failure and presents the emergence of decentralized oracle capability from the dual ledger design as well as native support for non-fungible digital assets.– NESS Network: Low-power hardware hence sustainable
– EmerNVS: General purpose Name-Value System to store data and digital assets
– Skywire: End-to-end (e2e) encrypted mesh VPN
Backed by such natives features, NESS doesn’t rely on any centralized protocols and short of shutting down the entire Internet we would be at loss to find anyone or anything that could interfere with it.
2.2 Uniqueness & Determinacy
Repeatedly generating and selecting a biased random number is not expected for the security-sensitive applications that rely on randomness. Uniqueness is a stricter requirement than determinacy. Determinacy only requires that the random generation procedure involves no randomness.
2.3 Non-interactiveness
On the blockchain, it is natural to generate random numbers in a decentralized way. However, the communication overhead will become a limitation or a single point of failure of the whole system. ‘ Elliptic Curve Digital Signature Algorithm (ECDSA) can be redefined to satisfy determinacy but not uniqueness and communication overhead can lead to single-point-of-failure of the whole system.
|
Group size |
Tolerable node failure |
System failure |
|
51 |
24.2% |
0.0105% |
|
101 |
31.1% |
0.0104% |
|
201 |
36.7% |
0.0106% |
|
501 |
41.6% |
0.0108% |
Source: https://arpa.medium.com/arpa-threshold-bls-random-number-generator-design-2b7a6e7f7826
With PrivateNess decentralized PKI and operations the group size is utility rather than metric; it can scale up or down indifferently, node failure can be All but 1 block publisher theoretically, the chain will run in read only mode even if block-publisher goes offline and even then it wouldn’t affect existing services, System failure are mitigated between 2 blockchains running battle-tested tech (Emercoin, Genesis 2013 and Skycoin, Genesis 2014).
2.4 We don’t put all our Trust in the same basket
Emercoin URIs are BIP21 and due to it’s extremely light footprint, Emercoin daemons are running on all incentivized PrivateNess nodes. That’s how we are resistant to Phantom nodes like the PIVX and all masternode systems that can run Golang forks. In smart contract environments, randomness sources that satisfy the uniqueness, determinacy and non-interactiveness imply relatively complex aggregation mechanisms and consensus to protect the consumer’s trust in the system.
With PrivateNess we turn tables on Trust versus System versus Decentralization. Who should trust what, and why should anyone trust anything when not necessary? We empower the consumer as much or as little as desired, depending on the privateness and ownership of the seedkey used to initialize the non-repeating 1536 bits entropy PRNG. The consumer can be a human, a smart contract or both in such a way that any cryptographic system will recognize (or not if malicious).
- Acquire or Register a Non-Fungible PrivateNess asset for randomness depending on uniqueness of seedkey used at PRNG initialization.
- Subscribe to Randomness with the ID obtained earlier: Initialize PRNG with seedkey;
- Initiate a Randpay tx with 1/1 Risk to pay with short timeout to force an onchain event; for when 3rd party need to verify origin and unbiasedness
Note: This Private and Public seedkey approach make for a simpler and lighter implementation of BLS signatures for consensus verifiable by 3rd parties; and outsourced to a foreign blockchain secured by Bitcoin hash power through merged-mining PoW.
2.5 More about UHE-PRNG
It uses a “safe prime” factor to guarantee that every possible PRNG “state” is visited before the sequence begins to repeat. The result is that the “period” of this generator will be the “Germain prime” 1,768,863 x 2E1535 – 1, which is approximately 2.132 x 10E468. This is such a large number that it might as well be infinite.
You find our Ultra High Entropy Pseudo Random Number Generator on GitHub: https://github.com/NESS-Network/PyUHEPRNG
2.6 This generator effectively never repeats
For our purposes, a “SeedKey” is used to initialize the PRNG to a pseudo-randomly chosen point in this incredibly large loop of unpredictable pseudo-random numbers, from which we then pull as many pseudo-random values as we need. The 256-character “SeedKey” uses the 94 printable ASCII characters (spaces are ignored). Therefore, this yields 94E256 possible seedkeys. This is 1.32 x 10E505 possible strings, which is equivalent to 1,678 bits of entropy. Since this is greater than the total entropic state of the UHEPRNG, a SeedKey of this length and complexity is sufficient (and necessary) to fully initialize a PRNG of this complexity.
Not only is it an extremely good pseudo-random number generator, it is also extremely fast.
This makes its use with slow processors, or under interpreted languages (such as its implementation language, JavaScript) much more practical than many other much weaker PRNGs. Although mathematicians have been unable to determine how many different 26×26 Squares can be created, they have been able to determine that the number is at least 9.337 x 10E426, or approximately 2E1418. This is an incredibly large number. But for our purposes it is only meaningful if any of those many possible Latin Squares could potentially be generated by our OTG grid generator. If we were to use any traditional PRNG, even something state-of-the-art such as Fortuna, based upon a cryptographic symmetric cipher or a hash, we would be limited to generating Latin Squares from such a generator’s much lower level of entropy . . . on the order of 256 or 384 bits. This would be more than sufficient for many cryptographic applications, but not for ours. Since 26×26 Latin Squares are known to have a potential entropy of at least 1418 bits, we needed a PRNG that could keep up. So an “ultra-high entropy” PRNG, having an entropy of 1536 bits, was developed to allow access to all possible Latin Squares.
Not only do we want a system that is able to select one OTG grid from among the truly incredible number of possible Latin Squares, but every user needs to be able to regenerate their own personal one out of 10E427 grids if their existing paper copy should ever need to be replaced, resized, recolored, re-fonted, or reprinted for any reason. We achieve those two goals by generating and capturing a very long 1536-bit pseudo-random number — the “SeedKey” — then using that number to set the ultra-high entropy pseudo-random number generator’s 1536-bit “initial state” from which a single unique grid will be created.
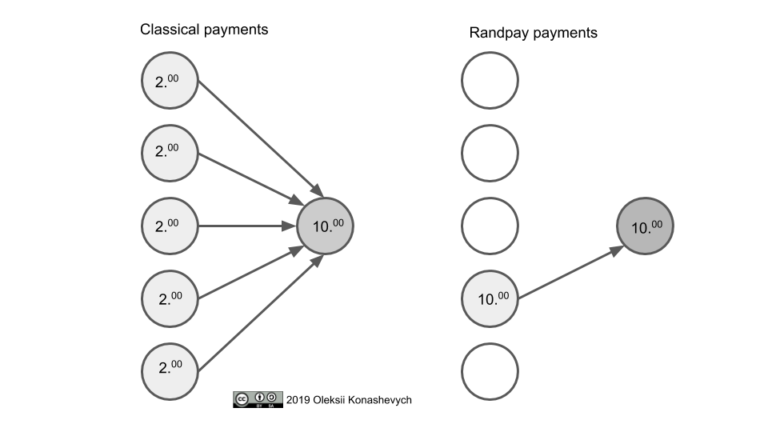
2.7 More on Randpay
Transactions on Emercoin blockchain are non-monetary for the most part so far and near-free. This article describes a system for aggregating payments based on a zero-trust lottery protocol. We demonstrate its applicability to very large-scale settlements amounting to trillions of transactions per year. Under the protocol, the payment recipient creates a unique payment address and defines a space of possible payment addresses including this one.The payer chooses a random address from the specified space, creates a payment transaction to the selected address, and then sends the transaction to the payment recipient.
If the address specified in the received transaction matches the previously created one, the recipient signs the transaction and publishes it to the blockchain, and payment is transferred. If the addresses do not match, the transaction is deemed invalid and is ignored; only 1 in $risk trigger payment; or on demand with a 1 on 1.
In a typical Randpay scenario, the payment is unlikely in each particular “lottery” instance. But as the number of such instances is high, the balances of all participants will be updated in a fair way. This article presents a mathematical model proving that, for all the participants, Randpay will statistically converge to the fair amounts they would have received or sent without using this subsystem. In addition, Randpay reduces payers’ transaction costs, making it economically viable, especially for micro payments.
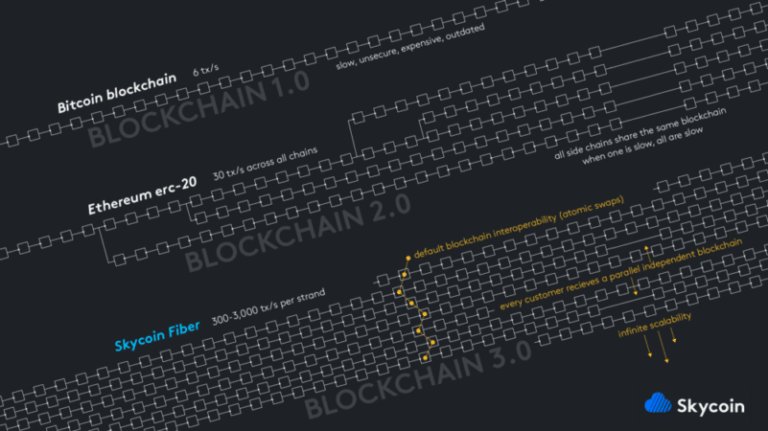
3. Main Platform: Skycoin Fiber
Full Featured language based on Golang and a secondary coin hour currency named NCH (NESS Coin Hours) minted 1:1 every hour of holding in a non-custodial wallet. NCH are used to pay for transactions. NESS/NCH is like NEO/GAS, VET/VTHOR, THETA/TFUEL
Skycoin was entirely built from scratch to address BTC and ETH consensus and scalability problems by developers of both projects. Additionally, Fiber provides Skywire, an end-to-end encrypted dark mesh VPN faster than TCP/IP inside the mesh perimeter through the use of Multi Protocol Label Switching (MPLS).
4. EmerNVS for Blockchain-as-a-Service
Emercoin offers an impressive collection of sub-systems, such as encrypted Key/Secrets Keeping, DNS and SSL with near-zero fees. EMC is also a non-fungible coin. Anything that can be identified by a SHA-256 hash can be recorded as digital, tradable, unique asset.
EmerNVS stores data in the blockchain by a set of name -> value pairs
Name = label for the stored data, up to a length of 512 bytes.
Value = the data itself, up to a length of 20*1024 (20kb).
Emercoin allocates up to 20kB for value, enough to fit public keys for most modern cryptographic applications. We consider a cryptocurrency blockchain to be an extremely reliable place to publish and maintain public keys for many cryptographic applications such as SSH/SSL certificates. Like regular payment transactions, NVS pairs stored in the blockchain also get confirmations during block generation, and are virtually immune to being altered by a ‘Man-in-the-Middle’ attack.
Since the blockchain is a trusted data store protected from unauthorized modification, it is a great foundation for the deployment of cryptographic Public Key Infrastructure (PKI), Digital Proof-of-Ownership (DPO), immutable record keeping, timestamps, and other distributed services.
5. CoreNode authentication by NFTs
- 5.1 Proof of ownership
In order to guarantee the absolute authenticity of our CoreNodes in the PrivateNess Network ecosystem and to eliminate any security breach, we have integrated a feature allowing authentication by verified NFT which guarantees the authenticity of CoreNodes. This certificate of authenticity will be required so that the CoreNodes can perform all forms of operations required on the Fiber Chain.Unlike traditional masternodes where operators must lock a considerable amount of native coins in order to keep their masternode active, the Fiber Chain technology behind the NESS blockchain does not require it. Instead, we have implemented a certification of authenticity in the form of NFT which guarantees that each operator has the required collateral amount needed. NESS coins used to create NFT certificates will automatically be locked. This NFT certificate, which is equivalent to a unique value of 20,000 NESS, will be available on our Marketplace and/or by OTC. There will be no limit to the amount of certificates issued as long as the total available supply of NESS is respected. This certificate could also be sold for a one-off amount of 20,000 NESS by the owner when he decides to deactivate his CoreNode.In everyday life, you can compare these ‘Certificates of Authenticity for CoreNodes’ as title deeds. They ensure that the property is yours and that you can buy it or dispose of it as you see fit. Only the value in fiat can fluctuate depending on the supply and demand of native NESS coins on the market.
- 5.2 Differences between mining and masternodes
Since masternodes can do much more than regular nodes, running them also requires a more significant investment. However, those who run masternodes are rewarded by earning a portion of block rewards. Depending on the network, masternode operators may be rewarded once or several times per day. However, it is essential to understand that running a masternode is not equivalent to mining. Masternodes are no extension of Proof-of-Stake, where cryptos are not mined but staked. This is also not true, as Proof-of-Work projects can utilize masternodes as well.Running a masternode allows operators to generate a passive income by holding coins, which is a method similar to how stakes work in PoS. The income earned by running a masternode depends on a variety of factors, such as the node’s uptime, reliability, speed and bandwidth.Anyone can run a masternode.
6. NESS coin supply distribution
The PrivateNess Network includes a native coins called NESS. This coin will be used for all operations on the blockchain and will have a maximum of 165 Millions coins supply without any possibility of increase in the future.
|
Budget |
NESS |
|
Open market distribution |
65.000.000 |
|
CoreNodes rewards |
50.000.000 |
|
Team reserve |
30.000.000 |
|
Development & marketing budget |
20.000.000 |
|
Total supply: |
165.000.000 |
7. Roadmap 2021 – 2022
- 2021 Q3 13
Rest of the year 2021 we consolidate pending hard-fork to CX when the platform allows it. In the meantime, we’re giving the NESS Coin Hours ($NCH) their own listing and pair with Skycoin’s SCH hence jump starting the coin hours economy in shape and form.– Coin Hours and support assets listings on BitShares XBTS Innovative Feed of Verifiable Randomness Functions with Coin Hours as renewable payment commodity.
– Introduction of “Locked NESS” subscription payment model
– KISS 1-click node deployment (containers)
– KISS Prototyping DPN; Wireguard with SSL supporting any upstream network
– KISS Prototyping zero-trust proxy/gateway services
- 2021 Q4 14
Revenues:– NESS Rewards activation
– Opt-In Skyminers Rewards
– Enable XBTS DeFi and Liquidity pools
- 2022 Q1 14
With respect to hardware availability and early investors interest:– Real world implementation of exportable, sustainable wireless solutions with deterministic privacy suitable for isolated and/or hostile environments now or in 1000 years.
– Community suggested initiatives and special projects
8. Sources & Further Reading
-
Net neutrality is dead — what now? https://www.theverge.com/2018/6/11/17439456/net-neutrality-dead-ajit-pai-fcc-internet
-
Cyberbalkanization and the Future of the Internets https://medium.com/skycoin/cyberbalkanization-and-the-future-of-the-internets-f03f2b590c39
-
Avoiding Blockchain Balkanization https://consensys.net/research/avoiding-blockchain-balkanization
-
The new tech totalitarianism https://www.newstatesman.com/culture/books/2019/02/new-tech-totalitarianism
-
Picture Panopcticon: https://commons.wikimedia.org/wiki/File:Penetentiary_Panopticon_Plan.jpg
-
Epilogue: Digital Roads to Totalitarianism https://link.springer.com/chapter/10.1007/978-3-030-00813-0_7
-
Skywire – the foundation of a new internet – is fast, private, secure and self sustaining https://www.reddit.com/r/skycoin/comments/9coq80/skywire_the_foundation_of_a_new_internet_is_fast
-
The Emercoin NVS https://emercoin.com/en/documentation/blockchain-services/emernvs
- What Is Entropy In Cryptography? https://qvault.io/cryptography/what-is-entropy-in-cryptography
- About the Emercoin Blockchain http://emercoin.com/en/tech-solutions
- What Are The 7 Layers Of The OSI Model? https://www.webopedia.com/reference/7-layers-of-osi-model/#OSI-7
- What is ECDSA Encryption? How does it work? https://www.encryptionconsulting.com/what-is-ecdsa/
- Randpay. Large-scale micropayment subsystem based on the Emercoin cryptocurrency. https://medium.com/@emer.tech/randpay-6a028f16c82a